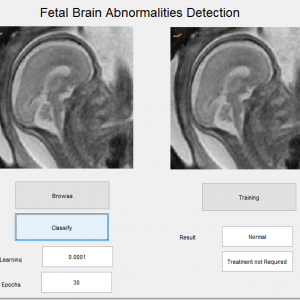
Description
Image Forgery Detection using Matlab
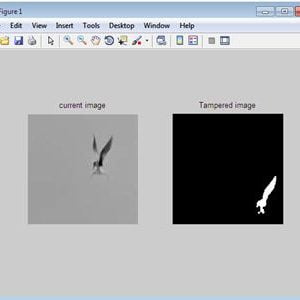
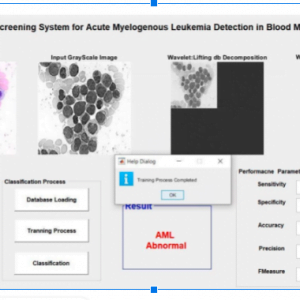
Copy-move is one of the most commonly used methods of tampering with digital images. Key point-based detection is recognized as effective in copy-move forgery detection (CMFD). This paper proposes an efficient CMFD method via clustering SIFT key points and searching similar neighborhoods to locate tampered regions. In the proposed method, the key points are clustered based on scale and color, grouped into several smaller clusters, and matched separately, which reduces the high time complexity caused by matching caused by the high dimensionality of SIFT. By using image splicing and image sampling the proposed method is superior to existing state-of-art methods in terms of matching time complexity, detection reliability
Image Forgery Detection using Matlab
INTRODUCTION TO FORGERY DETECTION
Imitations are not new to humanity however as an opportunity is very old trouble. In the beyond it changed into restrained craftsmanship and writing but did now not have an effect on the overall population. These days, due to the headway of automatic image handling software programs and changing gadgets, an image can be results managed and changed. It is alternatively tough for people to apprehend outwardly whether or now not or now not the photo is unique or manipulated. There is a speedy increment in digitally controlled falsifications in great media and on the Internet. This sample shows authentic vulnerabilities and abatements of the credibility of digital photographs. In this manner, growing techniques to check the honesty and realness of the superior snapshots is essential, especially considering that the pictures are delivered as evidence in a courtroom docket of regulation, as facts things, as part of restorative records, or as coins related opinions. In this revel in, image forgery detection is one of the critical purposes of photograph forensics. The most essential goal of this paper is: To present numerous elements of photograph forgery detection; to assess some overdue and modern methods in pixel-primarily based absolutely picture forgery detection; to give a comparative examination of modern techniques with their benefits and downsides. The rest of the paper is prepared as follows. An assessment of photo forgery detection has been presented in the first segment. In the second segment, we speak about a particular form of virtual photograph forgery. In the third phase, we present a virtual photograph forgery detection method. In the fourth Section, we introduce and talk approximately unique present strategies of pixel-based completely image forgery detection, especially duplicate-float. A comparison of numerous detection algorithms is given in the fifth phase and the remaining section gives the notion of this paper. Image Forgery Detection using Matlab
Existing Systems
- Error level analysis detection technique
- Colour filter array detection technique
Drawbacks of Exisitng System
- Poor Edge detection.
- Less accuracy
- It is not suitable for all lighting conditions images
Proposed System
- Copy-Move forgery,
- Image splicing
- GLCM feature extraction
- Pre-processing
- Clustering
Advantages
- Better efficiency and less sensitive to noise
- Better accuracy
- Processing time is less
- The proposed copy-move forgery detection scheme can achieve much better detection result
Image Forgery Detection using Matlab
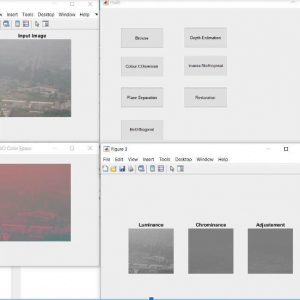
Block diagram
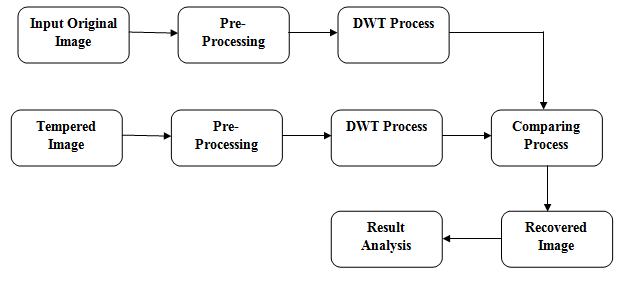
Block Diagram Explanation
Image Forgery Detection using Matlab
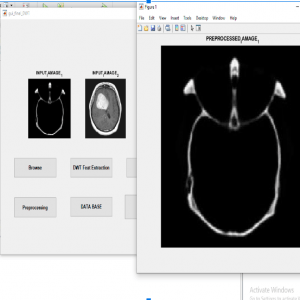
PREPROCESSING
Image recuperation is the operation of taking a corrupted/noisy photograph and estimating the smooth unique photograph. Corruption might probably also to be had much bureaucracy on the side of motion blur, noise, and digital camera misfocus.? Image healing isn’t like photo enhancement in that the latter is designed to emphasize the capabilities of the photo that make the photograph extra captivating to the observer but no longer constantly supply sensible information from a systematic difficulty of view. Image enhancement techniques (like evaluation stretching or de-blurring by the nearest neighbor approach) supplied thru “Imaging packages” use no a priori version of the manner that created the image.? With photo enhancement noise may be successfully removed by using sacrificing some choice, but this isn’t suitable in many programs. In a Fluorescence Microscope selection inside the z-route is terrible as it is. More advanced image processing techniques ought to be carried out to get higher the item.? De-Convolution is an example of a picture recovery approach. It is able to: Increase decision, especially within the axial route removing noise developing evaluation.
Image Forgery Detection using Matlab
Discrete Wavelet Transform (DWT)
The discrete wavelet remodels (DWT) became superior to using the wavelet rework to the digital international. Filter banks are used to approximate the behavior of the non-prevent wavelet remodels. The sign is decomposed with an immoderate-skip smooth out and a low-bypass clear out. The coefficients of these filters are computed using mathematical evaluation and made to be had to you. See Appendix B for more records about those computations.
2.2 Discrete Wavelet Transform
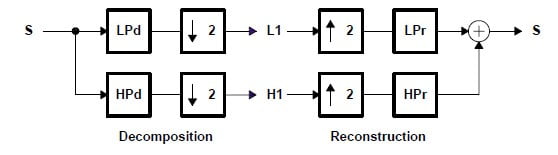
Where,
LP d: Low Pass Decomposition Filter
HP d: High Pass Decomposition Filter
LP r: Low Pass Reconstruction Filter
HP r: High Pass Reconstruction Filter
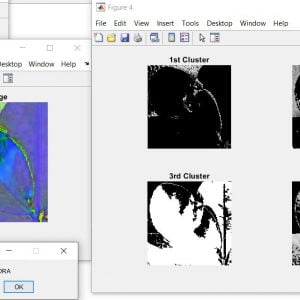
Clustering
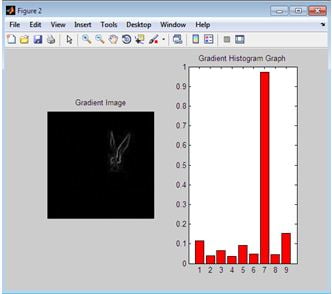
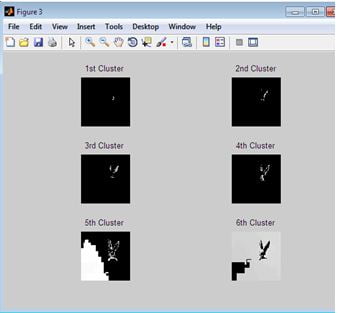
Clustering can be taken into consideration as the most crucial unsupervised learning problem so,? it offers to find a form in a collection of unlabeled statistics. A cluster is therefore a set of items that might be? comparable? amongst them and are? extraordinary? to the items belonging to exceptional clusters
Clustering algorithms can be categorized as listed underneath
- Exclusive Clustering
- Overlapping Clustering
- Hierarchical Clustering
- Probabilistic Clustering
In the primary case, records are grouped in a one-of-a-kind way, in order that if a positive datum belongs to a unique cluster then it could not be blanketed in every other cluster. On the alternative the second kind, the overlapping clustering, uses fuzzy units to cluster information, simply so everything can also moreover furthermore belong to two or extra clusters with extremely good stages of the club. In this case, statistics can be related to the perfect club fee. A hierarchical clustering algorithm is primarily based completely totally on the union of the various 2 nearest clusters. The starting scenario is determined by setting every datum as a cluster. After some iteration it reaches the final cluster preferred
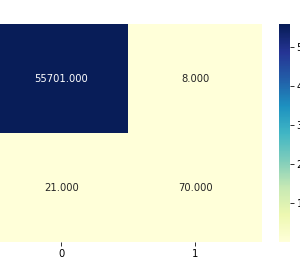
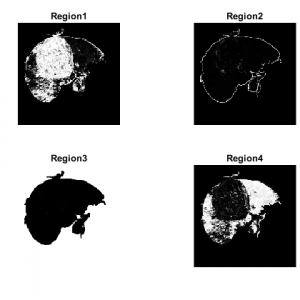
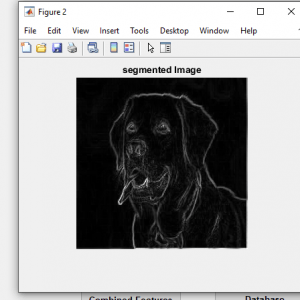
Comparing process
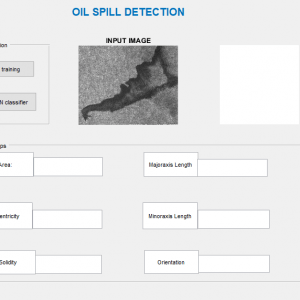
Here we are going to compare the input image and tempered image after the two processes. After the preprocessing and discrete wavelet transform we can get the image information after that in this process, we going to compare the images by means of
- Image Blocks and? image block features/labeled features
Image Blocks?
Indistinct?block?processing, you divide an? image? matrix into rectangular?blocks?and perform?image?processing?operations on the individual? blocks.?Blocks? start in the upper left corner and completely cover the image without overlap. If the? blocks?do not fit exactly over the image, then any incomplete? blocks? are considered partial blocks. a
Certain?image?processing?operations involve processing an? image?in sections, called?blocks?or neighborhoods, rather than processing the entire image at once. Several functions in the toolbox, such as linear filtering and morphological functions use this approach. By creating these image blocks on the image we can get some clarity to process the image and able to get some features from the image for that purpose we create the image blocks. After that, we can process and compare the image and then finally analyze the resulting image.
Requirement Specification
Hardware Requirements
- system
- 4 GB of RAM
- 500 GB of Hard disk
Software Requirements:
- MATLAB 2018b
REFERENCE:
[1] WeiqiLuo,Jiwu Huang, GuopingQiu, ?Robust Detection of RegionDuplication Forgery in Digital Image?, 18th IEEE International Conference on Pattern Recognition, Hong Kong, p. 746? 749, 2006.
[2] XiaoBing KANG, ShengMin WEI, ?Identifying Tampered Regions Using Singular Value Decomposition in Digital Image Forensics?, IEEE International Conference on Computer Science and Software Engineering, Wuhan, Hubei, p. 926? 930, 2008.
[3] Alin C Popescu and Hany Farid, ?Exposing Digital Forgeries by Detecting Duplicated Image Regions?, Dartmouth Computer Science Technical Report TR2004-515, USA, August 2004.
[4] Hwei-Jen Lin, Chun-Wei Wang And Yang-Ta Kao, ?Fast Copy-Move Forgery Detection?, WSEAS Transactions on Signal Processing, p. 188- 197, May 2009.
[5] HieuCuong Nguyen and Stefan Katzenbeisser, ?Detection of copy-move forgery in digital images using Radon transformation and phase correlation?, IEEE Eighth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Piraeu, 2012.
[6] Leida Li, Shushang Li, Hancheng Zhu, ?An efficient scheme for detecting Copy-Move forged images by local binary patterns?, Journal of Information Hiding and Multimedia Signal Processing, Vol. 4, No. 1, pp. 46-56, January 2013.
[7] Hailing Huang, Weiqiang Guo, Yu Zhang,?Detection of Copy-Move Forgery in Digital Images Using SIFT Algorithm?, IEEE Pacific-Asia Workshop on Computational Intelligence and Industrial Application, Wuhan, China, 2008.
[8] Seung-Jin Ryu, Min-Jeong Lee, and Heung-Kyu Lee, ?Detection of Copy-Rotate-Move Forgery Using Zernike Moments?, Information Hiding Lecture Notes in Computer Science Volume 6387, pp 51-65, 2010.
[9] Jessica Fridrich, David Soukal, and Jan Luk??, ?Detection of CopyMove Forgery in Digital Images?, Digital Forensic Research Workshop, Cleveland, Ohio, USA, 2003.
[10] YanjunCao ,Tiegang Gao , Li Fan , Qunting Yang, ?A robust detection algorithm for Copy-Move forgery in digital images?, Journal of Forensic Science International, p. 33? 43, 2012.














































































































































































































































































































































































































































































































































































































































































































































































Customer Reviews
There are no reviews yet.