Description
Spectrum Resource Allocation Algorithm Based On Joint Access Mechanism
ABSTRACT
This concept represents a solution with a cognitive radio network over the secondary users who are bound to the new network via external frequency sensing. Here is a flow-based approach for network selection for secondary users in cognitive radio networks. Most approaches in the current literature on cognitive radio do not consider network selection is not established over the secondary users to select. This concept represents a network flow framework for network selection. The approach shown can enable re-assignment of networks to secondary users and also re-assignment of channels to secondary users within the same network and accessing of external accessing network systems. The assignments and re-assignments take into account, the interference caused to primary users, the price each secondary user is willing to pay and the quality of service (QoS) obtained by each secondary user in the external networks systems. the allocation happens between the secondary and primary. Spectrum sharing performs well under the conditions that the interference to the PU is assured to be less than a certain threshold. Non-orthogonal multiple access (NOMA) has attracted considerable interests in recent years, which is seen as an important wireless access scheme for the coming 5G wireless communication system. Simultaneous wireless information and power transfer (SWIPT) is proposed as a popular technique to extend the operation duration of power-supply-limited wireless networks. Spectrum Resource Allocation Algorithm Based On Joint Access Mechanism
Spectrum Resource Allocation Algorithm Based On Joint Access Mechanism
INTRODUCTION
In this paper, we propose a secure cooperative communications scheme for orthogonal frequency division multiple access (OFDMA) cognitive radio networks (CRNs) where a primary base station (PBS) wants to transmit information to some distant primary users (PUs) in the presence of a set of passive eavesdroppers. In our model, the transmission is performed in two consecutive time slots; in the ?rst time slot, PBS transmits while secondary users (SUs) and the eavesdroppers listen. In the second time slot, SUs transmit while PUs, secondary base station (SBS), and the eavesdroppers listen. We consider two schemes for eavesdropping; in the? In the first scheme, the eavesdroppers listen to transmissions from the PBS to SUs, and in the second scheme, we assume that the eavesdroppers apply the maximal ratio combining approach to the received signals in the ?rst and the second time slots for the primary network. In proposed model, SUs are allowed to use the licensed spectrum of PUs as long as they help PUs to satisfy their secrecy rate requirement. We assume a frame-based transmission where each frame is divided into two consecutive time slots of equal duration. In the ?rst time slot, PBS transmits while the SUs as well as the eavesdroppers listen. In the second time slot, the selected SUs relay the PBS information to the distant PUs. Meanwhile, SUs use the remaining resources to transmit their own information to the SBS while eavesdroppers listen to this transmission. We formulate our proposed schemes as an optimization problem and solve it by dual Lagrange approach. We evaluate our proposed scheme in various situations using simulations and show the ef?ciency of the proposed scheme. An important aspect of the proposed paradigm is that replacing the conventional average interference threshold constraint by the primary secrecy rate constraint does not only decrease the secondary average secrecy rate with respect to the conventional case, but this can actually provide signi?cantly higher secondary average secrecy rate. The licensed spectrum always performs low utilization, and existing resources cannot be utilized effectively. Cognitive radio (CR) as an emerging technology is proposed to provide a high spectrum The associate editor coordinating the review of this manuscript and approving it for publication was Min Jia. utilization, in which SUs are allowed to access the spectrum when PU is absent. Spectrum sensing (SS) can achieve better sensing performance when the probability of detection Pd is higher meanwhile the probability of false alarm Pf is lower. However, SS will consume some system resources and decrease the system performance. Simultaneous wireless information and power transfer (SWIPT) can harvest the radio frequency (RF) signal energy to supply energy consumption.Spectrum Resource Allocation Algorithm Based On Joint Access Mechanism
Spectrum Resource Allocation Algorithm Based On Joint Access Mechanism
EXISTING METHOD
- Primary users are considered to be network individuals single.
- Decode and forward relay
DRAWBACKS
- The spectrum channel obtained may identifies low SNR over the network and hard to attain the efficient data on much needed time.
PROPOSED SYSTEM
- Efficient Signal transmission over the primary and secondary users system with efficient network selection with interference consideration and throughput efficiency analysis over multiple primary and secondary users system using several codes.
- Cognitive radio (CR) as an emerging technology is proposed to provide high spectrum through the Simultaneous wireless information and power transfer (SWIPT) Technique.
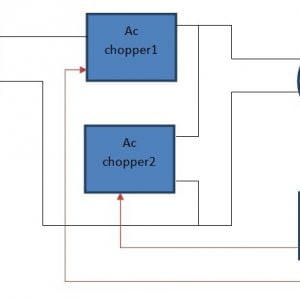
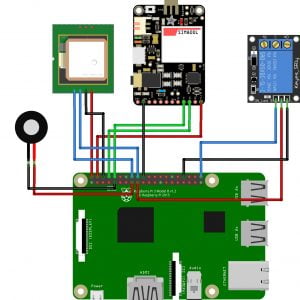
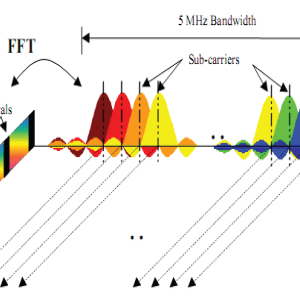
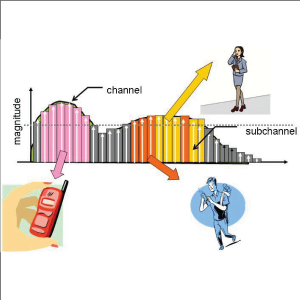
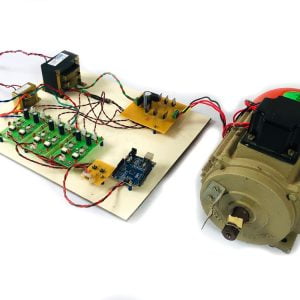
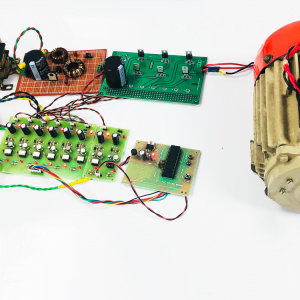
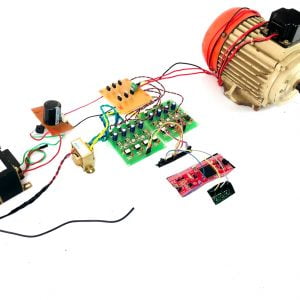
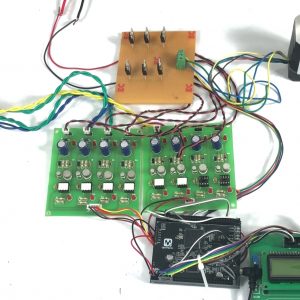
Fig: Network consideration
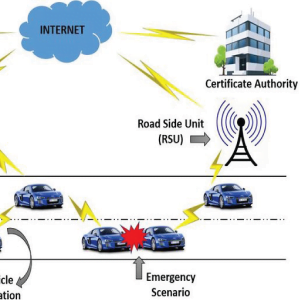
Fig: SU Network selection
PROPOSED METHOD EXPLANATION:
One from the base station, and one from the near user who is acting like a relay. Thus, we can expect the outage probability of far user to decrease. This concept is called cooperative communication/cooperative relaying. We can see that NOMA naturally allows cooperative communication because the near user has the far user’s data because it must decode it anyway. we used user cooperation where the near user acted as a relay to the far user. This user cooperation was natural because the near user has the far user’s data anyway. But does the near user have enough power to relay that data? What if relaying drains the near user’s battery? This is where RF energy harvesting could help.
TYPES OF ENERGY HARVESTING
There are two main energy harvesting protocols namely,
- Time switching
- Power splitting
Let’s briefly see about these two techniques
- Energy harvesting by Time Switching
Here, the device operates in a time-slotted fashion. During the first fraction of time-slot, the device harvests electromagnetic energy from its surroundings. This harvested power is used for transmission in the next fraction of time-slot. We will see more about time-switching in future posts. In this post, we will see how to implement power-splitting protocol for cooperative NOMA.
- Energy harvesting by Power Splitting
Here, the device splits the received signal power for energy harvesting and information decoding. Unlike time switching, where separate time slots are required for both processes, power splitting allows simultaneous implementation of energy harvesting and information decoding. So, this method is also called SWIPT – Simultaneous Wireless Information and Power Transfer.
Fig 3: Network model of cooperative SWIPT NOMA
ADVANTAGES
- Decision-based sensing and acquiring the available spectrum over the network leads to analyzing the network available in front of the system and is feasible to attain a much high data rate over the networks
- The licensed spectrum always performs low utilization, and existing resources cannot be utilized effectively [9]. Cognitive radio (CR) as an emerging technology is proposed to provide high spectrum The associate editor coordinating the review of this manuscript and approving it for publication was Min Jia. utilization, in which SUs are allowed to access the spectrum when PU is absent. Spectrum sensing (SS) can achieve better sensing performance when the probability of detection Pd is higher meanwhile the probability of false alarm Pf is lower. However, SS will consume some system resources and decrease the system performance. Simultaneous wireless information and power transfer (SWIPT) can harvest the radio frequency (RF) signal energy to supply energy consumption
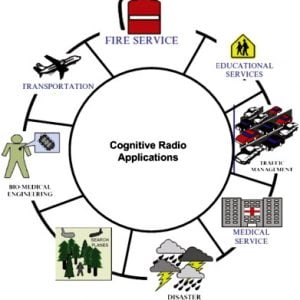
APPLICATIONS
- Urgently needed data transfer application
- Networks under people much unreachable area
SOFTWARE REQUIREMENT
- MATLAB 7.8 or above versions
REFERENCES
[1] S. Haykin,?Cognitive radio: brain-empowered wireless communications,? IEEE Journal on Selected Areas in Communications, vol. 23,
- 2, pp. 201? 220, February 2005.
[2] Y. Li and A. Nosratinia, ?Hybrid opportunistic scheduling in cognitive radio networks,? IEEE Transactions on Wireless Communications,
vol. 11, no. 1, pp. 328? 337, January 2012.
[3] Z. Shi, T. Tan, K. C. Teh, and K. H. Li, ?Energy-efficient cognitive radio network based on multiband sensing and spectrum sharing,? LET
Communications, vol. 8, no. 9, pp. 1499?1507, June 2014.
[4] O. Simeone, I. Stanojev, S. Savazzi, Y. Bar-Ness, U. Spagnolini, and R. Pickholtz, ?Spectrum leasing to cooperating secondary ad hoc networks,? IEEE Journal on Selected Areas in Communications, vol. 26, no. 1, pp. 203?213, January 2008.
[5] W. D. Lu, Y. Gong, S. H. Ting, X. L. Wu, and N. T. Zhang, ?Cooperative OFDM relaying for opportunistic spectrum sharing: Protocol design and resource allocation,? IEEE Transactions on Wireless Communications, vol. 11, no. 6, pp. 2126?2135, June 2012.
[6] M. I. Rahman, A. Behravan, H. Koorapaty, J. Sachs, and K. Balachandran. ?License-exempt LTE systems for secondary spectrum usage: scenarios and ?rst assessment.? in IEEE Symposium on New Frontiers in Dynamic Spectrum Access Networks (DySPAN), pp. 349-358, 2011.
[7] A. Babaei, J. Andreoli-Fang and B. Hamzeh. ?On the impact of LTE-U on Wi-Fi performance.? in 2014 IEEE 25th Annual International Symposium on Personal, Indoor, and Mobile Radio Communication (PIMRC), Washington DC, pp. 1621-1625, 2014.
[8] S. Y. Lien, J. Lee and Y. C. Liang. ?Random Access or Scheduling: Optimum LTE Licensed-Assisted Access to Unlicensed Spectrum.? IEEE Communications Letters, vol. 20, pp. 590-593, Mar. 2016.
[9] H. Cui, V. C. M. Leung, S. Li and X. Wang. ?LTE in the Unlicensed Band: Overview, Challenges, and Opportunities.? IEEE Wireless Communications, vol. 24, pp. 99-105, 2017.
[10] A. Mukherjee et al.. ?Licensed-Assisted Access LTE: coexistence with IEEE 802.11 and the evolution toward 5G.? IEEE Communications Magazine, vol. 54, pp. 50-57, Jun. 2016.
[11] F. M. Abinader et al.. ?Enabling the Coexistence of LTE and Wi-Fi in Unlicensed Bands.? IEEE Communication Magazine, vol. 52, pp. 54-61, Nov. 2014.
[12] B. Ren et al.. ?Cellular communications on the license-exempt spectrum.? IEEE Communication Magazine, vol. 54, pp. 146-153, May. 2016.
[13] J. Jeon et al.. ?LTE in the unlicensed spectrum: Evaluating coexistence mechanisms.? in 2014 IEEE Globecom Workshops (GC Wkshps), Austin, TX, pp. 740-745, 2014.
[14] R. Yin, G. Yu, A. Maaref and G. Y. Li. ?LBT-Based Adaptive Channel Access for LTE-U Systems.? IEEE Transactions on Wireless Communications, vol. 15, pp. 6585-6597, Oct. 2016.
[15] Y. Li, J. Cheng and Q. Li. ?Enhanced listen-before-talk scheme for frequency reuse of licensed-assisted access using LTE.? in Proc. PIMRC, Hong Kong, pp. 1918-1923, Aug. 2015.













































































































































































































































































































































































































































































































































































































































































































































































Customer Reviews
There are no reviews yet.