Description
Objective: –
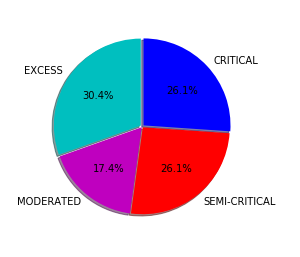
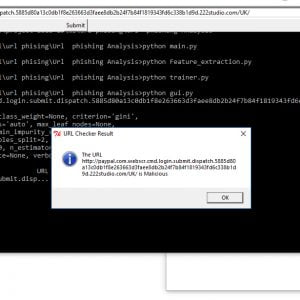
The detection and mitigation of phishing attacks is a grand challenge due in the real world. There have been numerous studies on detecting and mitigating Phishing attacks. Phish Limiter is an effective and efficient solution to detect and mitigate phishing attacks with an accuracy of 98.39%.
Detecting Phishing Attacks using NLP and Machine Learning
Abstract: –
With the advancement of communication and social media, the phenomenon of fake news is advancing at a rapid and increasing rate. Fake news identification is a new study subject that is attracting a lot of attention. However, due to a lack of resources, such as datasets and processing and analysis methodologies, it confronts several difficulties.
In this paper, we offer a machine learning-based approach for detecting fake news. As a feature extraction strategy, we used the term frequency-inverse document frequency (TF-IDF) of a bag of words and n-grams, and as a classifier, we used Support Vector Machine (SVM). To train the suggested system, we additionally present a dataset of fake and authentic news. The obtained results demonstrate the system’s efficiency. Detecting Phishing Attacks using NLP and Machine Learning
Introduction: –
- Phishing has become one of the deadliest attacks. There are various approaches to thwarting phishing attacks from Associate in nursing infrastructure viewpoint such as Phish net, lexical-based online learning, and a proactive phishing identification approach.
- In addition, traditional ways to discourage phishing e-mails square measure through the use of vendor-based solutions like acanthopterygian Email Security entree and Symantec electronic communication entree, but each system need e-mail traffic redirection to every security appliance
- Though trafficker solutions could determine phishing e-mails, they are doing not stopping Associate in Nursing users from clicking on a malicious link inside a flagged e-mail which will lead to compromising a computer system. To discourage such considerations, one proposes a range of Intrusion Detection Systems (IDS) and Intrusion hindrance Systems (IPS) approaches to distinguishing and deterring phishing e-mails, however, they lack feasibility or can’t be used once e-mail communication becomes encrypted, that is usually done these days
The existing model of the system: –
Phishing has been proven to be one of the devil’s creations and a terrifying environment for internet communities. Organizations that handle the PHI data of thousands of people, such as health insurance, will need to be less vulnerable to phishing attacks. Many firms’ employees are through suitable training programs to avoid becoming victims of this curse. Many of these businesses have used phishing scenarios to demonstrate to staff how cyber thieves steal sensitive information or use deception to install dangerous software. As implied by the name, which sounds similar to fishing, it’s a means to gain access to personal information such as ID and passwords by impersonating a legitimate business. People can protect themselves from phishing attempts by installing and updating reliable security software on a regular basis.
Proposed model of the system: –
- Methods to Mitigate Phishing Attacks
- Natural Language Processing
- Porter Stemming Algorithm
- Tokenization, Parsing, and Case Folding
- Machine Learning
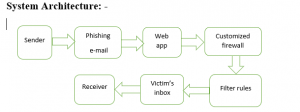
Description
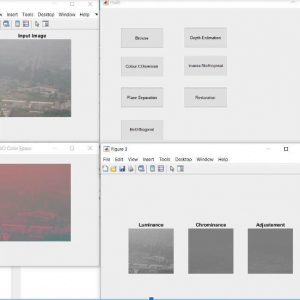
The accompanying diagram depicts the system architecture for identifying phishing attempts. This application was created for a corporation or organization where the admin and employees can log in using their individual user ids and passwords. Adding an employee, setting filter policies, settings, user removal, grading, and logout are all available on the admin dashboard. When a new employee starts working for the company, the employee’s name, joining date, type of employment, contact address, user type, pan card number, and contact number are all entered. The employee is provided an e-mail address from the organization’s subdomain and a light-weight Directory Access Protocol (LDAP) server is configured. An employee code is produced automatically. Filter policies are specified by the administrator based on the company’s needs, and mails containing policy phrases are blocked. The suggested application gives the company the opportunity to downgrade or upgrade filter policies, and the administrator can change the firewall configuration at any moment.
A light-weight Directory Access Protocol (LDAP) server is configured and the employee is given an e-mail address from the organization’s subdomain. A code for each employee has generated automatically. Filter policies are defined by the administrator depending on the needs of the firm, and emails that contain policy terms are blocked. The proposed program allows the organization to downgrade or upgrade filter policies, and the firewall configuration can be changed at any time by the administrator.

































































































































































































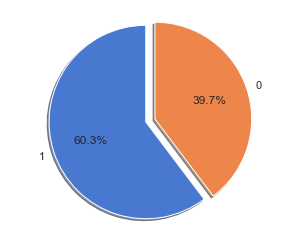
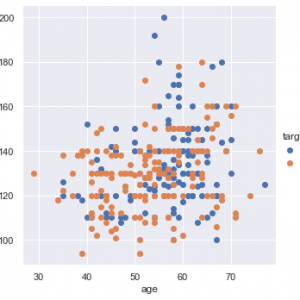
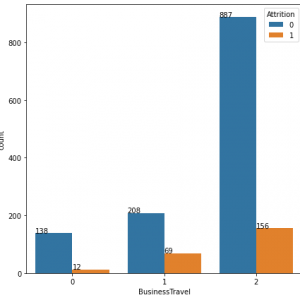











































































































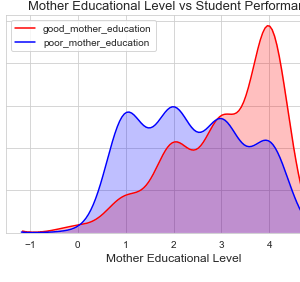
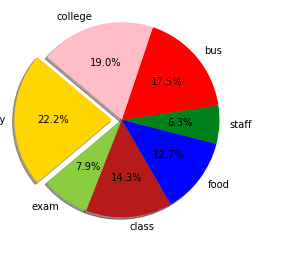
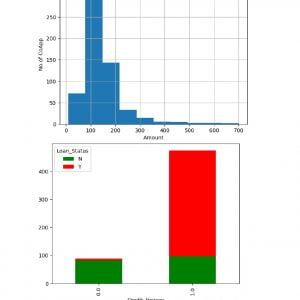
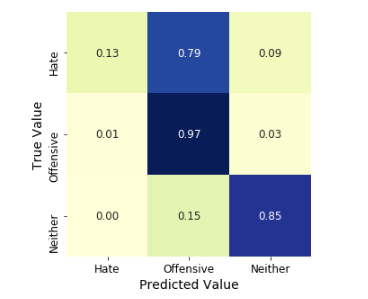


































































































































































































































































































































































































































































Customer Reviews
There are no reviews yet.